Don't Get Hacked! Essential Kubernetes Security with Nessus & Kube-bench
Lock Down Your Kubernetes Cluster: Initial Access & Vulnerability Scanning
Let's talk Kubernetes security! Some of you may have seen me write about Kubernetes before, but for those who haven't had the chance to delve in, here's the gist: Kubernetes (K8s) is like the conductor of an orchestra, orchestrating containerised applications in a dynamic and scalable way. It's become the go-to platform for deploying cloud-native applications.
But just like any complex system, Kubernetes comes with its own set of security challenges. And as we discussed in previous newsletters, securing initial access to your cluster is paramount.
But what happens after an attacker gains access? That's where vulnerability scanning comes in.
MITRE ATT&CK®
What is MITRE ATT&CK®? Think of the MITRE framework as a playbook for understanding cyberattacks. It breaks down the attacker's lifecycle into various tactics and techniques. Vulnerability scanning plays a crucial role in the "Discovery" tactic, helping you identify weaknesses that attackers might exploit to gain a foothold or move laterally within your environment. You can read more on it here.
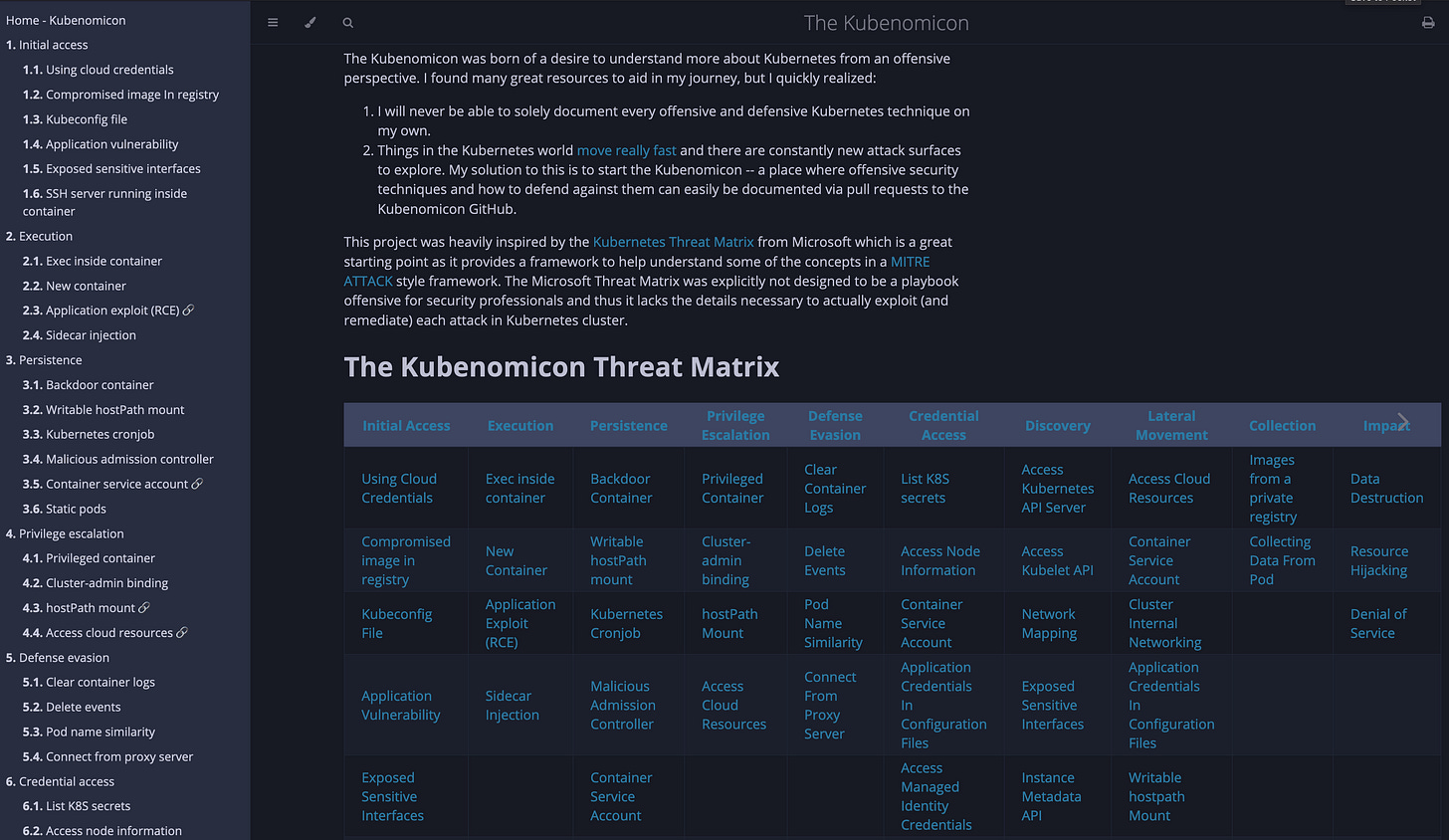
Initial Access: The Kubernetes Challenge
Breaking into a Kubernetes cluster is often the toughest hurdle for attackers. It usually boils down to exploiting common weaknesses, like:
Vulnerable Applications: Think of it as sneaking in through a window left ajar. Attackers exploit vulnerabilities in the applications running inside your containers.
Supply Chain Attacks: Imagine a Trojan horse hidden in a delivery. Attackers compromise container images in your registry, injecting malicious code that gets deployed within your cluster.
Exploiting Developer Tools: This is like stealing the keys from under the doormat. Attackers target developer resources like Kubeconfig files or exposed sensitive interfaces to gain unauthorised access.
Cloud Credentials: The master key to the entire castle! Leaked cloud credentials can give attackers complete control over your Kubernetes environment.
Before we dive any deeper: I've contributed to the Kubernetes Security Encyclopaedia along with the maintainer Graham Helton, featuring my latest contributions with detailed attack examples and defensive techniques.
A Multi-Layered Approach to K8s Security
To effectively secure your Kubernetes environment, you need a multi-layered approach:
Secure Configurations: Tools like Kube-scan and Kube-bench help you identify misconfigurations and ensure compliance with security best practices.
Node-Level Security: Traditional vulnerabilities at the operating system and application level can still be exploited. This is where distributed vulnerability scanning with Nessus comes in.
Kube-bench: Your Kubernetes Configuration Watchdog
Imagine Kube-bench as a meticulous inspector, carefully examining your Kubernetes cluster for any security gaps or misconfigurations. It's an open-source tool that checks your cluster against the CIS Kubernetes Benchmarks, a set of security best practices designed to harden your deployments.
How Kube-bench Works in Practice
Benchmark Selection: Kube-bench automatically detects your Kubernetes version and selects the appropriate CIS Benchmark.
Configuration Checks: It analyses your cluster's configuration files, settings, and deployments, comparing them against the benchmark recommendations.
Detailed Reporting: Kube-bench generates a comprehensive report highlighting any deviations from the benchmark, including specific recommendations for remediation.
Why Kube-bench Matters
Compliance: Helps you meet regulatory requirements and industry standards by ensuring your cluster adheres to security best practices.
Misconfiguration Detection: Identifies potential security weaknesses caused by misconfigurations, which attackers could exploit.
Hardening: Provides actionable guidance on how to strengthen your cluster's security posture and reduce your attack surface.
Scaling with Nessus and Tenable
Imagine your Kubernetes environment expanding with hundreds of nodes across multiple clusters. Managing individual scans becomes a real headache. That's where Nessus comes in.
Here's how distributed scanning with Nessus and Tenable.sc works in a Kubernetes environment:
Agent Deployment: Deploy Nessus agents as containers on each worker node using a DaemonSet.
Scan Execution: Agents perform local scans, collecting vulnerability data from the node's operating system and applications.
Data Aggregation: Agents send scan results to a heavy forwarder within the cluster.
Data Processing: The heavy forwarder compresses and optimises the data before sending it to the indexers.
Centralised Indexing: Indexers store and index the vulnerability data for efficient searching and analysis.
Reporting and Analysis: Access vulnerability data through Tenable.sc's web interface, generate reports, and analyse trends.
Key Takeaways
Don't just focus on the control plane. Secure your worker nodes with distributed vulnerability scanning.
Embrace a multi-layered approach. Combine configuration scanning, node-level scanning, and centralised management for comprehensive security.
Stay proactive. Regularly scan your environment and remediate vulnerabilities to stay ahead of attackers.